AWS -Virtual Private Cloud
VPC Networking Components
VPC Networking Components
We can use following VPC components to configure our VPC:
Internet Gateway
Virtual Private Gateway
Customer Gateway
VPN Connections
NAT Gateway
Route Table
Internet Gateway
There is an Internet Gateway(IGW) attached to every VPC to connect the resources within a VPC to the internet. One IGW can be attached to a VPC at any given point of time. IGW is a must for any VPC to allow its resources to connect to the internet.
Virtual Private Gateway and Customer Gateway
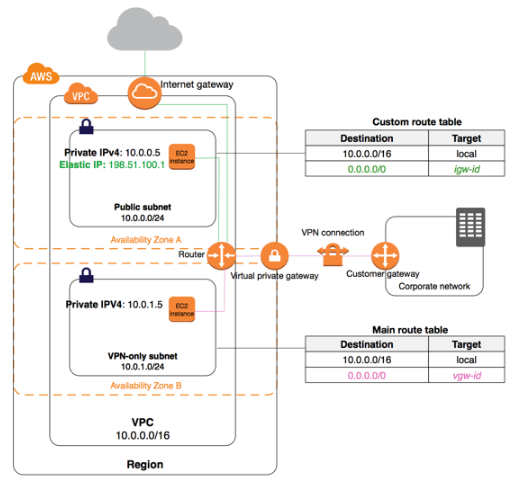
"To link the customer network to Amazon Virtual Private Cloud we need to use an optimal Amazon VPC VPN connection. A Customer Gateway is the anchor on our side (customer side) of that connection. The anchor on the AWS side of this VPN connection is called a Virtual Private Gateway."[1]
The two tunnels #1,#2 in the Virtual Private Gateway are to provide increase availability of Amazon VPS service. Suppose, if there is a device failure within AWS, your VPN connection automatically fails over to the second tunnel so that your access isn't interrupted. From time to time, AWS also performs routine maintenance on the virtual private gateway, which may briefly disable one of the two tunnels of your VPN connection. Your VPN connection automatically fails over to the second tunnel while this maintenance is performed. It's therefore important to configure both tunnels along with customer gateway.
The following diagram illustrates your network, the customer gateway, the VPN connection that goes to the virtual private gateway, and the VPC.

we can also create additional VPN connections to other VPCs using the same customer gateway device. When you create a VPN connection, the VPN tunnel comes up when traffic is generated from your side of the VPN connection. To protect against a loss of connectivity if your customer gateway becomes unavailable, you can set up a second VPN connection.
Creating AWS Virtual Private Gateway and VPN connections:
- Open AWS console
- Go to VPC Dashboard
- Click on Virtual Private Gateways under VPN and click on Create Virtual Private Gateway
AWS Virtual Private Network (AWS VPN) lets you establish a secure and private tunnel from your network or device to the AWS global network.
You can connect your Amazon VPC to remote networks and users using the following VPN connectivity options:
| VPN connectivity option | Description |
|---|---|
| AWS Site-to-Site VPN | You can create an IPsec VPN connection between your VPC and your remote network. On the AWS side of the Site-to-Site VPN connection, a virtual private gateway provides two VPN endpoints (tunnels) for automatic failover. You configure your customer gateway on the remote side of the Site-to-Site VPN connection. |
| AWS Client VPN | AWS Client VPN is a managed client-based VPN service that enables you to securely access your AWS resources in your on-premises network. With AWS Client VPN, you configure an endpoint to which your users can connect to establish a secure TLS VPN session. This enables clients to access resources in AWS or an on-premises from any location using an OpenVPN-based VPN client. |
| AWS VPN CloudHub | If you have more than one remote network (for example, multiple branch offices), you can create multiple AWS Site-to-Site VPN connections via your virtual private gateway to enable communication between these networks. |
| Third party software VPN appliance | You can create a VPN connection to your remote network by using an Amazon EC2 instance in your VPC that's running a third party software VPN appliance. AWS does not provide or maintain third party software VPN appliances; however, you can choose from a range of products provided by partners and open source communities. |
You can also use AWS Direct Connect to create a dedicated private connection from a remote network to your VPC. You can combine this connection with an AWS Site-to-Site VPN to create an IPsec-encrypted connection.
NAT Gateway
For the resources in Private subnet to gain access to the internet- you need a Network Address Translator(NAT) Gateway/Instance. NAT Gateway sits in the public subnet and the resources in private subnet should have a route to NAT Gateway(there has to be a local route for the traffic flow in between the subnets in the Route table). So the outbound traffic that comes to the NAT gateway from the private subnet is sent to the internet as if it originates from NAT instance. For the inbound traffic from the internet.
Route tables
A Route table contains set of rules, that is used to determine where the network traffic from subnet is directed.
Each subnet in VPC must be associated with a route table, which controls the routing for that subnet. You can explicitly associate a subnet with a route table. Otherwise, the subnet is implicitly associated with the main route table. A subnet can only be associated with one route table at a time, but you can associate multiple subnets with the same route table.
Routes:
Each route in a table has two fields destination and a target. For example, consider the below route table,
| Destination | Traget |
|---|---|
| 0.0.0.0/0 | igw-12345678901234567 |
The destination for the route is 0.0.0.0/0, which represents all IPv4 addresses. The target is the internet gateway that's attached to your VPC.
Every route table contains a local route for communication within the VPC. This route is added by default to all route tables. If your VPC has more than one IPv4 CIDR block, your route tables contain a local route for each IPv4 CIDR block. If you've associated an IPv6 CIDR block with your VPC, your route tables contain a local route for the IPv6 CIDR block. You cannot modify or delete these routes.
Main route table:
When we create a VPC, a main route table will be automatically created. The main route table controls the routing for all subnets that are not explicitly associated with any other route table. We can also create a custom route table. By default, when we create, a custom route table will be empty we can add routes as needed.
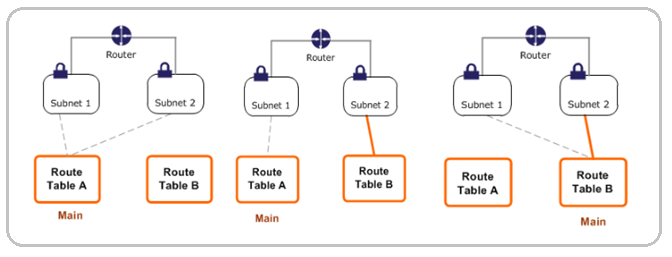
You can add, remove, and modify routes in main route table and custom route table. We cannot delete a main route table, but we can replace it with a custom route table. We can delete a custom route table only if there are no subnets associated with it.